Sysdig Falco is an open source behavioral activity monitoring tool for
better container security. It can detect anomalous activities occurring
on a Linux host as well as inside of a running container and supports
Docker orchestration tools like
Kubernetes and
Mesos.
Intrusion prevention vs. detection
Let us first understand two different aspects of security in software
systems i.e. intrusion prevention and intrusion detection. Intrusion
prevention is to stop an intruder from gaining an unauthorized access to
your environment. For example, role-based access control, two-factor
authentication, firewall rules etc. help in preventing intrusion.
But, what if in spite of all the security in place an intruder has
successfully breached the walls of container security? This is where
intrusion detection techniques come to the rescue. Sysdig Falco is one
of the tools which helps in intrusion detection. Falco detects
suspicious, anomalous activities that may occur inside a running
container on intrusion (for ex. spawning of a shell in a container
deployed on production environment; opening of sensitive files like
“/etc/shadow” in read/write mode; overwriting of binary files placed
in “/bin” or /usr/bin directories; mounting sensitive files/directories
inside the containers; unexpected tcp port has been opened/accessed and
much more)
Container Security
Sysdig Falco is an auditing and monitoring tool, and it does not enforce
any actions that will fix a problem. As such it can detect anomalous
behaviors and notify it to the users in different ways such as by
logging, notifications etc., but it won’t take any action for you. If
we have to draw an analogy the CCTV security systems would be pretty
close which helps detect intrusion but would not itself take any action.
The action has to be taken by a human who is watching the stream. Or in
today’s world, machine learning will aid you in by showing you important
frames from the stream but the action has to be taken by someone.
Detecting Anomalous Behavior!
Falco lets you define highly granular rules in a standard format. These
rules are checks for activities involving various things such as files,
containers network etc. For each of the checks, Falco uses a kernel
module which captures the stream of calls made and compares them with
the rules defined by the user (The module itself is installed with Falco
container image as explained here).
What kind of rules you want to define might vary based on your needs,
but Falco also comes with a rich set of rules for many commonly used
applications.
How does Falco work?
Falco runs in user space, using a kernel module (named sysdig_probe)
to intercept system calls and these calls are pushed into user space.
The user context (PID, thread ID, session ID etc.) is added to the
system calls to create events which are then compared against the rules
defined (in /etc/falco_rules.local.yaml). In case of a violation of a
rule, Falco notifies the user via the configured way (logging, email,
slack). One of the benefits of a user space implementation is being able
to integrate with external systems like Docker orchestration tools like
Kubernetes and Mesos.
Install Falco
Falco needs kernel headers installed on the host operating system.
Debian: apt-get -y install linux-headers-$(uname -r)
RHEL : yum -y install kernel-devel-$(uname -r)
Now, Falco image can be pulled and executed:
docker pull sysdig/falco
docker run -i -t --name falco --privileged -v /var/run/docker.sock:/host/var/run/docker.sock -v /dev:/host/dev -v /proc:/host/proc:ro -v /boot:/host/boot:ro -v /lib/modules:/host/lib/modules:ro -v /usr:/host/usr:ro sysdig/falco
Detecting anomalous activities:
While running you will notice that the Falco container itself downloads
a set of rules and run it within the container. We will use this to try
out the rules locally without needing a separate/dedicated setup.
Tue Nov 27 17:59:16 2018: Falco initialized with configuration file /etc/falco/falco.yaml
Tue Nov 27 17:59:16 2018: Loading rules from file /etc/falco/falco_rules.yaml
Tue Nov 27 17:59:17 2018: Loading rules from file /etc/falco/falco_rules.local.yaml
In this small demo we will run the Falco container and do some
operations in the same container which we will notice in the logs of the
container. In a way, we are checking the container security from the
same container which is running Falco!
Assuming you have run the Falco locally, spawn a shell inside a
container. You may also want to keep the logs of the container being
tailed in another window so that we can watch events in real time.
` $docker exec -it falco sh `
` `
If you try to open a sensitive file in read/write mode: vim
/etc/shadow
` `
Move a binary inside the bin directory:
mv /bin/ls /bin/ls.hack
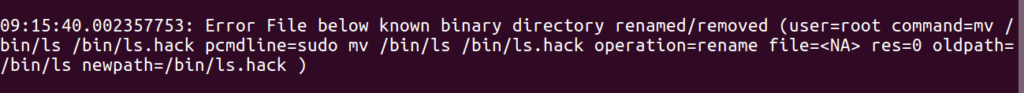
As you can notice for every operation which is not valid as defined by
the rule, it is logging in the logs.
Further reading
What we have covered is barely the surface of what Falco can do. Falco
has the concept of a macro which is similar to a function definition and
can be called from any rules file. While Falco comes with a bunch of
rules built in, you can also write a custom macro and define your logic
in it. Without going too deep into the technical areas, here are some
pointers to explore Falco further with some specific use case where
Falco is used.
- If you are wondering do you really need yet another additional tool
for container security or how does it compare with the likes of
Selinux or Seccomp and such similar tools then check out this great
post from Sysdig :
https://sysdig.com/blog/selinux-seccomp-falco-technical-discussion
- Falco can be used as an auditing tool for Kubernetes by using the
events of objects in Kubernetes. This can be very powerful for
auditing specific events in Kubernetes objects. The documentation
details this with an example:
https://github.com/falcosecurity/falco/wiki/K8s-Audit-Event-Support
- A set of default Falco ruleset for various applications:
https://github.com/draios/falco-extras
- Tne guide shows how to secure GKE cluster with Sysdig Falco:
https://cloud.google.com/blog/products/containers-kubernetes/securing-kubernetes-with-gke-and-sysdig-falco
Hope this blog was informational to you. You will enjoy Freddy’s recent post on Introduction to Kubernetes security using Falco.
Looking for help with cloud native security consulting & implementation? do check out our capabilities how we’re helping startups & enterprises as an cloud native consulting & services provider.